Google applauds the move to Rust because of the dramatic decrease in memory vulnerabilities

Google has Rust greeteda memory-safe programming language, as a key factor in its ability to reduce vulnerabilities as part of its Secure coding initiative.
Memory access vulnerabilities are common in programming languages that are not memory safe. In 2019, memory safety issues accounted for 76% of all Android vulnerabilities.
In response, many developers and technology giants are moving toward the use of memory-safe languages that will allow them to produce secure-by-design software and technology.
Vulnerabilities that rust away
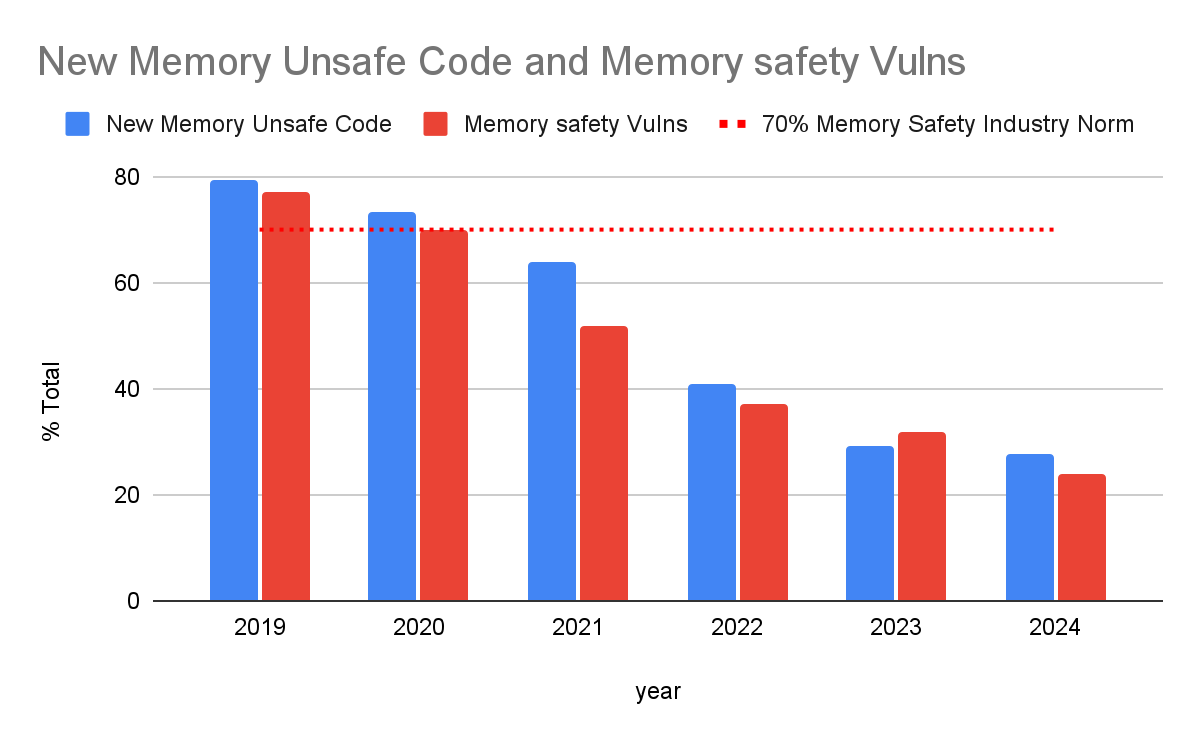
In its blog, Google presented a simulation of the transition to memory-safe languages through the gradual use of memory-safe code in new projects and developments over a five-year period. The results showed that despite a gradual increase in writing code in memory-insecure languages, memory safety vulnerabilities decreased significantly.
According to Google, this is because vulnerabilities are decreasing exponentially. New code written in insecure memory languages often contains bugs and vulnerabilities, but as the code is reviewed and refreshed, vulnerabilities are gradually removed, making the code more secure over time. Ergo, the main source of vulnerabilities is new code, and prioritizing the use of memory-safe programming languages when starting new projects and developments significantly reduces the number of vulnerabilities.
Google’s own shift to using memory-safe programming languages has seen a significant decline in the number of memory-related vulnerabilities, with the number of memory-safe vulnerabilities falling to 24% by 2024 – a stark contrast from 2019 and well below the industry standard of 70%. .
However, using memory-safe languages is not a panacea, and Google acknowledges that “in retrospect, it is clear that we have yet to achieve a truly scalable and sustainable solution that achieves an acceptable level of risk.”
Strategies for addressing memory security vulnerabilities have begun with reactive patching, where software manufacturers prioritize memory vulnerabilities, allowing other issues to be exploited more quickly.
The second approach involved proactive mitigation, where developers were encouraged to include mitigations such as stack canaries and control-flow integrity at the expense of execution speed, battery life, tail latencies, and memory usage. Developers were also unable to keep up with attackers’ ability to exploit vulnerabilities in new and creative ways.
In third place was proactive vulnerability discovery, with an emphasis on detecting vulnerabilities through fuzzing, which detects vulnerabilities based on the symptoms of an insecure memory. However, as Google notes, these tools are inefficient and time-consuming for teams to use and often do not catch all vulnerabilities, even with multiple attempts.
Google’s fourth tactic is therefore to engage in high-assurance prevention and secure-by-design development. By using programming languages like Rust, developers know and understand the properties of the code they’ve written and can deduce vulnerabilities based on those properties. This reduces costs for developers by reducing the number of vulnerabilities from the start, including vulnerabilities outside of memory security issues. This cumulative cost reduction also has the added benefit of making developers more productive.
“The concept is simple:,” the Google blog notes, “once we turn off the tap of new vulnerabilities, they decrease exponentially, making all our code more secure, increasing the effectiveness of security design, and eliminating the scalability issues that come with existing problems are alleviated. memory safety strategies in such a way that they can be applied more effectively and in a more targeted manner.”