Malware supplied via Facebook Crypto advertisements are silent unless you know that you are a valuable target
- Advertisement -
- Experts warn Facebook Crypto advertisements now deliver malware through trusted Merkinmoersing
- Malware only implements when victims meet specific browser or profile criteria
- Local Server and PowerShell assignments make stealthy data -sex filtration and control possible
A new wave of malware Attacks are aimed at Bitcoin and Crypto owners via Facebook advertisements that simulate familiar names in the industry.
Bitdefender says it has discovered a multi-phase malvertising campaign that has stripped the reputation of famous platforms such as Binance, TradingView, Bybit and others.
These malignant advertisements not only mislead users, they also adapt in real time to prevent detection and only deliver malware when the circumstances are ideal for the attackers.
Very evasive delivery system
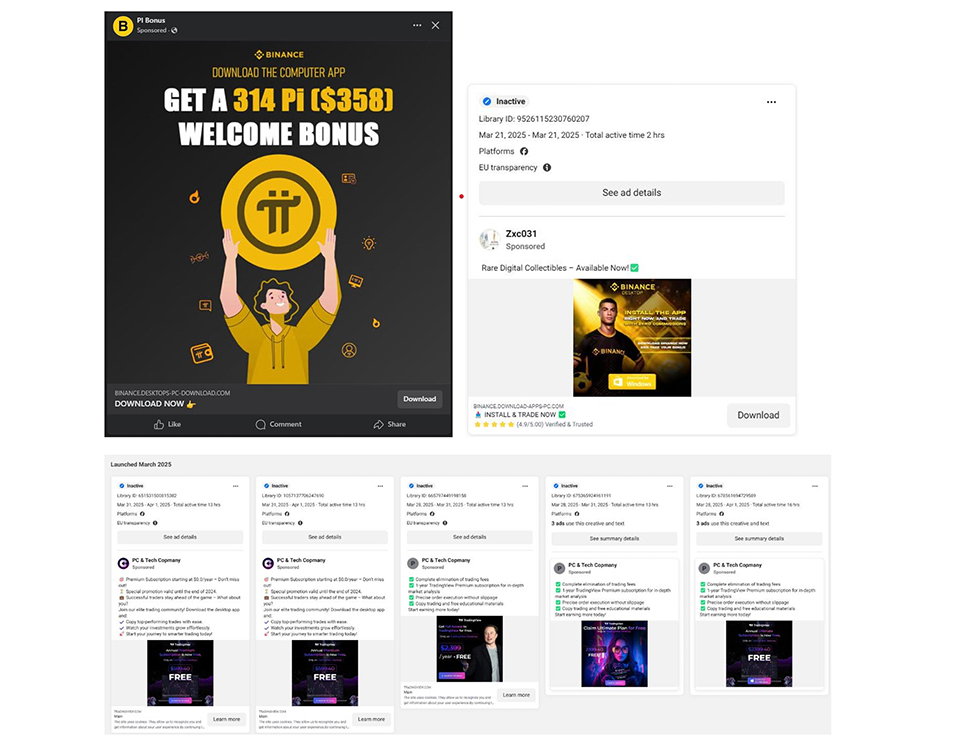
The schedule starts when cyber criminals hijack or make a Facebook accounts and use Meta’s advertising network to perform fraudulent promotions.
These advertisements contain fake offers and use photos of celebrities – Zendaya, Elon Musk and Cristiano Ronaldo are the usual suspects – to look more convincing.
Once clicked, users are diverted to look at websites that occur as legitimate cryptocurrency services and encourage them to download what a desktop client seems to be.
The malware delivery system is very evasive. Bitdefender says that the front-end of the fake site works with a local server that is quietly stored by the first installation, so that attackers can send payloads directly to the victim’s system and avoid most security software.
Delivery only happens if the victim meets specific criteria, as registered with Facebook, using a preferred browser such as Microsoft Edge, or matching a certain demographic profile.
Some malware examples run locally lightweight .Net servers and communicate with the website using advanced scripts that perform coded Powershell assignments. These can exfil sensitive data such as installed software, system and OS info and even GPU details.
Depending on the findings, the malware can download further payloads or simply sleep if it suspects that it is analyzed in a sandbox.
Bitdefender researchers found hundreds of Facebook accounts that promote these campaigns. They ran more than 100 advertisements in one day. Many advertisements focus on men aged 18 and older, with examples in Bulgaria and Slovakia.
How to stay safe

Investigate the advertisements carefully: Be very skeptical about advertisements that offer free crypto tools or financial benefits. Always check left before clicking.
Only download official sources: Visit platforms such as Binance of TradingView directly. Never Trust is diversions of advertisements.
Use left control tools: Tools such as Bitdefender Scamio or Link Checker can warn you about dangerous URLs before you are concerned.
Keep your UP -TO -TO -Date: Use one renowned antivirus This receives regular updates to catch evolving threats.
Watch out for suspicious browser behavior: Pages that are used to use the edge or irregularly diverse are huge red flags.
Report shady ads: Vlagous suspicious content on Facebook to help others prevent them from falling into the same fall.
Maybe you like it too
- Advertisement -



