Millions of voter documents leaked online – fears of election interference grow after breach

Voter IDs for 4.6 million Americans have been leaked online after being stolen from 13 databases that were not password protected.
The information in the databases included voter records, ballots, and election-related data, including personally identifiable information (PII), Social Security Numbers (SSN), driver’s license numbers, and voter ID numbers.
There are fears that the information could be misused for identity fraud, data theft, voter fraud and intimidation, and even election disruption.
Elections in jeopardy
The databases were found by cybersecurity researcher Jeremiah Fowler and subsequently reported to VPNMentorFowler used news articles and public information requests to identify a company called Platinum Technology Resource that was responsible for the exposed databases.
Fowler originally discovered a single unprotected database containing information from a single county in Illinois. However, when he replaced the county name in the database name, Fowler discovered 13 additional open databases, in addition to 15 that were not publicly accessible.
Platinum Technology Resource is a company that provides election-related services such as ballot printing and voter registration software, whose voter information portal is linked to the exposed databases and redirects to a domain labeled “Platinum vrms,” which Fowler says stands for “voter record management system.”
The exposed databases were reported to a partner company of Platinum Technology Resource called Magenium. They were subsequently blocked, but it is unknown how long the databases were exposed or who had access to them, with Fowler noting that “only an internal forensic audit could identify additional access or suspicious activity.”
During the 2020 election, claims were made on social media that votes had been cast in the names of deceased relatives. However, Fowler compared several exposed death certificates and found that none of the deceased were listed in active voter databases.
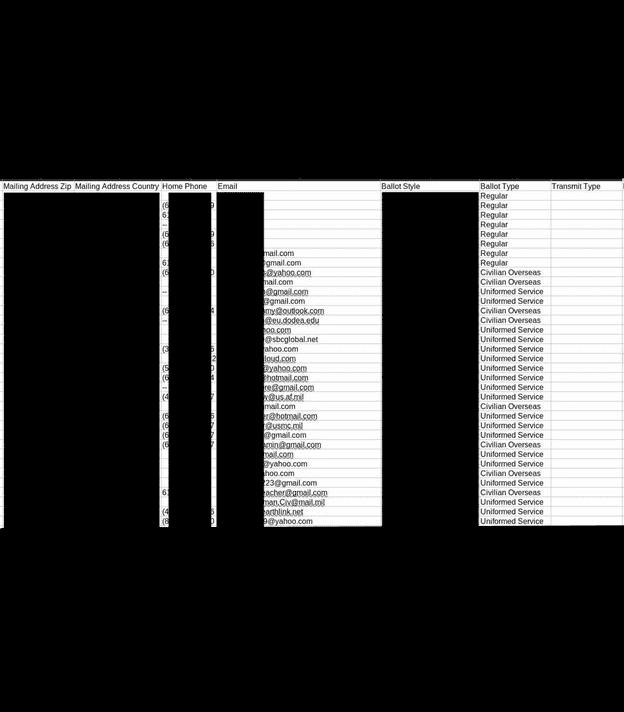
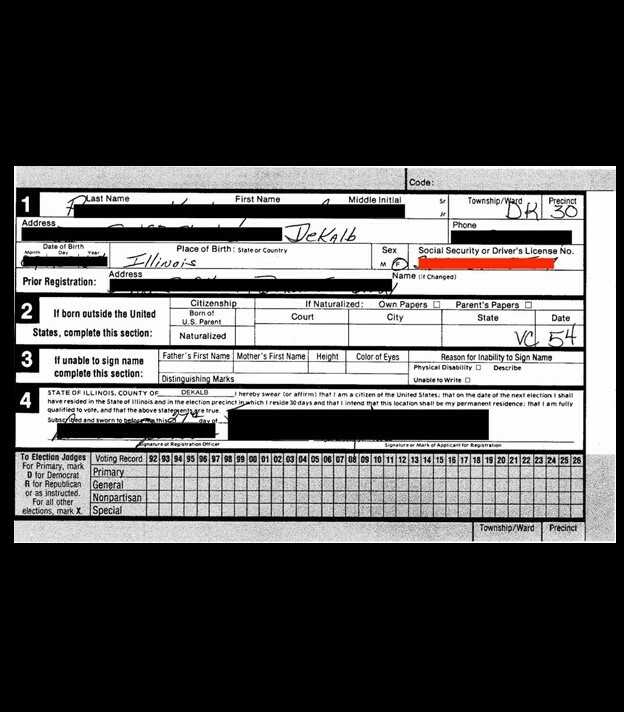
The other information exposed regarding those on the active voter rolls could have been used maliciously, as the information found in the databases included full names, physical addresses, some email addresses, dates of birth, SSN (full and partial) or driver’s license numbers, and historical voting records. There were also copies of voter registration applications, death certificates, and records of changes of address, jurisdiction, or state.
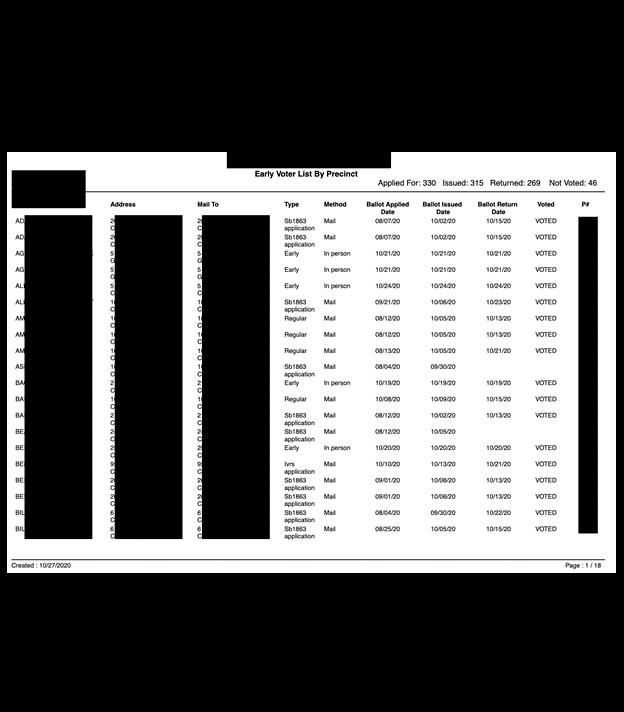
Additionally, candidate documents with personal phone numbers, email addresses, and home addresses were identified, as well as petitions with voter signatures, addresses, candidate loyalty oaths, economic interest, and additional supporting documentation. Fowler also discovered documents marked as official ballots for primary and general elections.
If these documents were accessible to nation states like Russia or China, or to political activists, they could be used to fuel mass disinformation campaigns or voter intimidation. There are also concerns that the information could be used by criminals to send out multiple mail-in ballots in the name of a single voter, sowing distrust in the electoral process and creating legal problems for the real voter whose name was used.
Fowler advises any organization that manages and stores sensitive information to follow cybersecurity best practices and use unique formats for database names to prevent someone from jumping from one database to another by simply replacing a single word, as Fowler did.