This sneaky fraud tactics uses deep trips to outsmart your favorite digital services
- Advertisement -
- Advertisement -
- Security experts say that traditional identity controls fail because they treat any verification as an isolated event
- Deppe variations with ease with ease of biometric biometric and liveliness
- Consortium validation shares data about organizations to detect subtle, repeated fraud attempts in real time
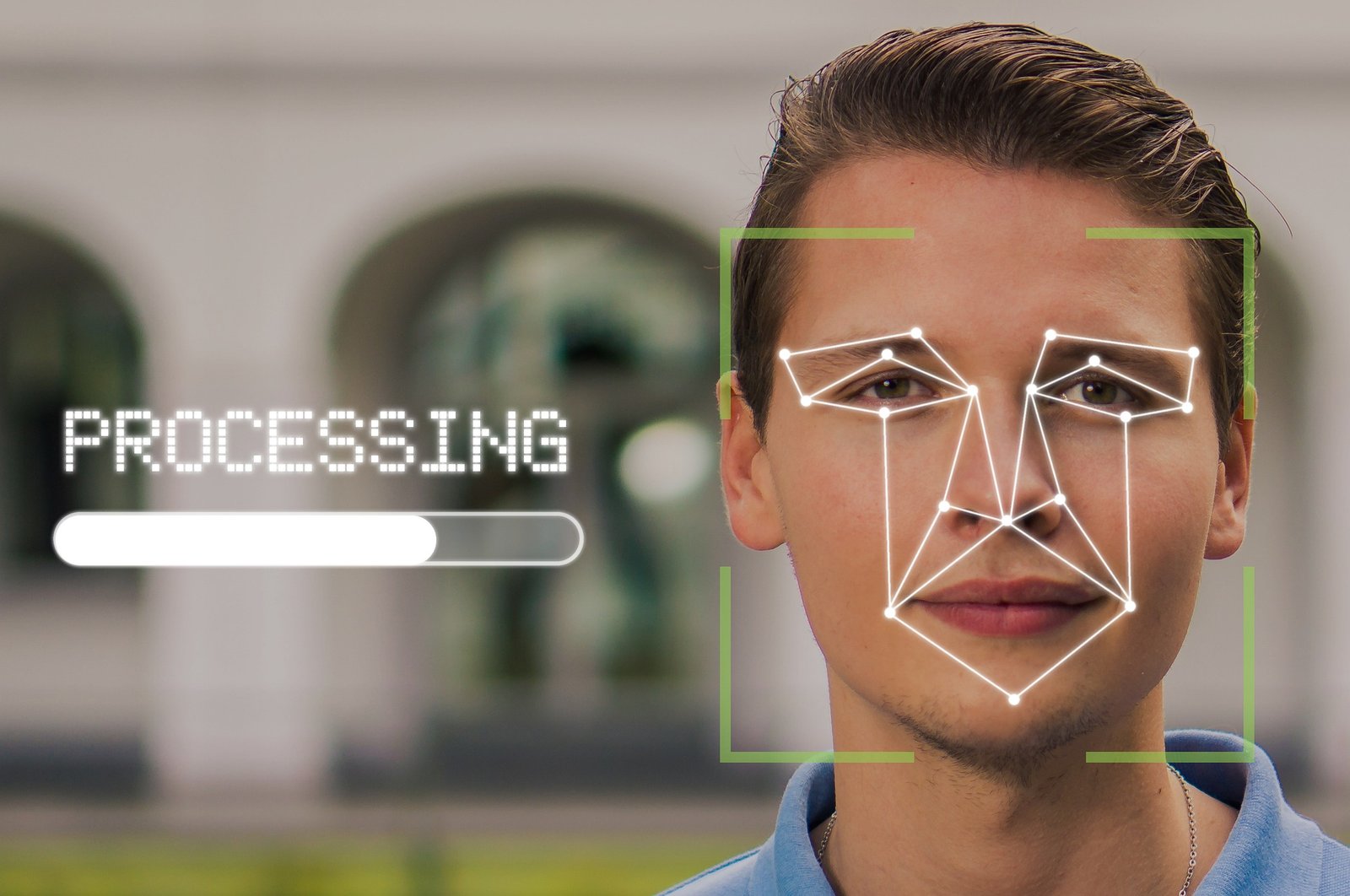
In a digital world, identity fraud is increasingly evolved by artificial intelligence in scale and sophistication.
Experts of AU10TIX have marked a new threat tactic that is known as “repeaters” that infiltrate the way in which fraudsters are reformed.
Unlike traditional attacks, they are not designed for immediate damage – instead, repeaters quietly test the defenses of banks, crypto platforms and other services using somewhat varied synthetic identities.
Once weaknesses have been identified, the same assets are re -used on several platforms in large -scale, coordinated fraud campaigns.
The core of this strategy is DeepFake-improved identities, somewhat modified versions of a core digital active.
These changes can include tweaks in facial features, background images or document numbers.
When it is investigated separately, each variation seems legitimate and often bypasses the traditional knowledge of your customer (KYC) processes and biometric controls.
The CEO of AU10TIX, Yair Tal, describes them as “The fingerprint of a new class of fraud: automated, AI-amplified attacks that reuse synthetic identities and digital assets to scale.”
What makes repeaters particularly dangerous is how they are gaps in the current fraud detection systems.
Most traditional defenses are based on static validation and evaluate every identity as an isolated event. Techniques such as biometric scans, light detection and ID checks often lack the wider image.
Because these synthetic identities are only submitted a few times per platform and seem unique, conventional tools are struggling to detect the repetition.
To prevent this threat, AU10TIX therefore introduces “consortium validation”. Unlike Siled Systems, this method can share several organizations identity signals in a real -time network, just like the Best end point protection platforms.
If an identity, or even a somewhat modified version, appears on more than one member organization, the system marks it immediately.
It is a partnership strategy that is aimed at connecting the points between other insulated incidents.
“We are proud to be paramount in detecting and blocking these attacks by advanced pattern recognition and real -time consortium validation,” Tal added
AU10TIX recommends organizations to also check for vulnerabilities for deepfakes and synthetic identities that can circumvent traditional KYC defenses.
It also recommends the close monitoring of behavior on devices, sessions and onboarding events, because it can reveal coordinated activities before they scale.
The best chance of early detection of such fraudulent activity is a connected and behavioral conscious security infrastructure because no solution can claim the Dear Antivirus or the Best Malware Protection Against this new generation of fraud.
Maybe you like it too
- Advertisement -